2025蓝桥网络安全 wp


Enigma
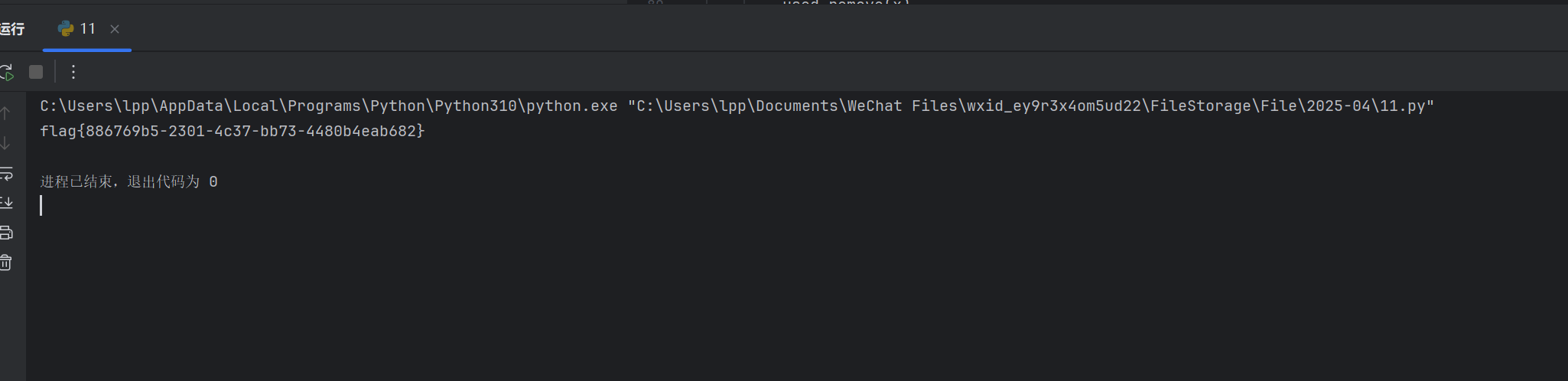
cyberchef倒过来直接出

flag{HELLOCTFERTHISISAMESSAGEFORYOU}
ShadowPhases
断点下在这里
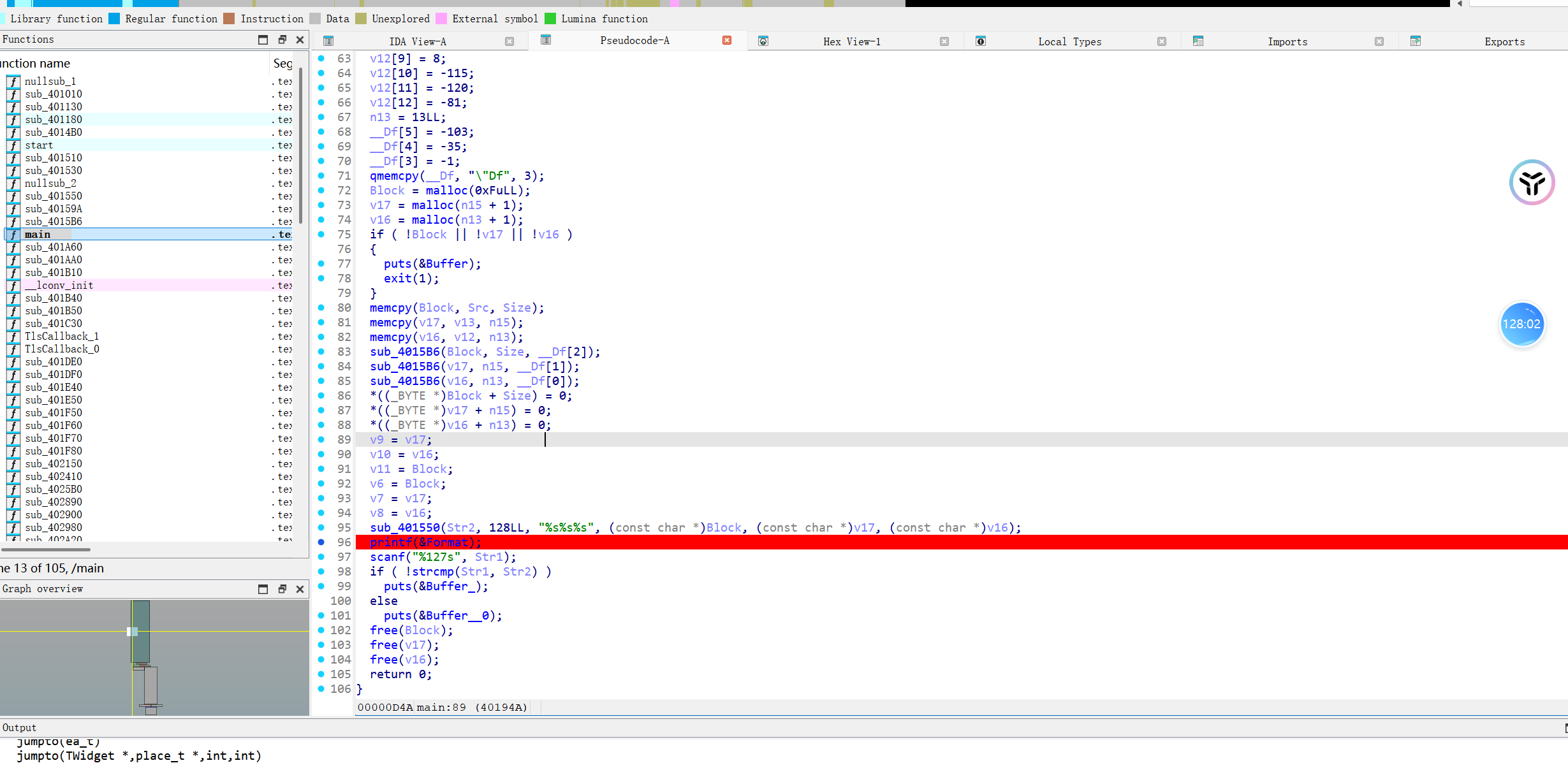
动调
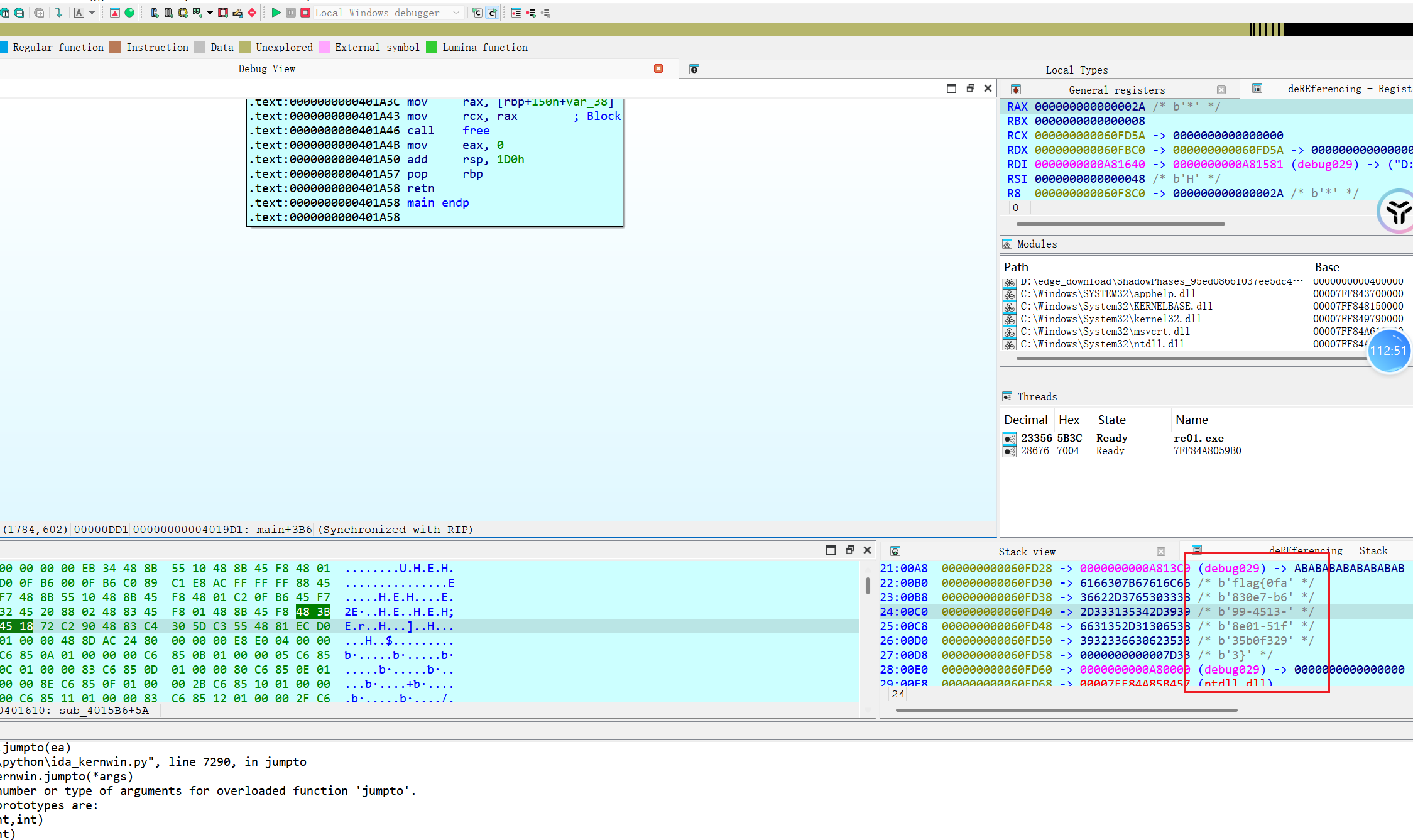
可以发现在右下角直接捕获flag
flag{0fa830e7-b699-4513-8e01-51f35b0f3293}
星际XML解析器
让输入xml,考虑xxe读flag出来
1 | <DOCTYPE data |

flag{3594e0ee-9fa3-4d66-871e-7f3c008b6d2e}
ezEvtx
日志分析,打开日志
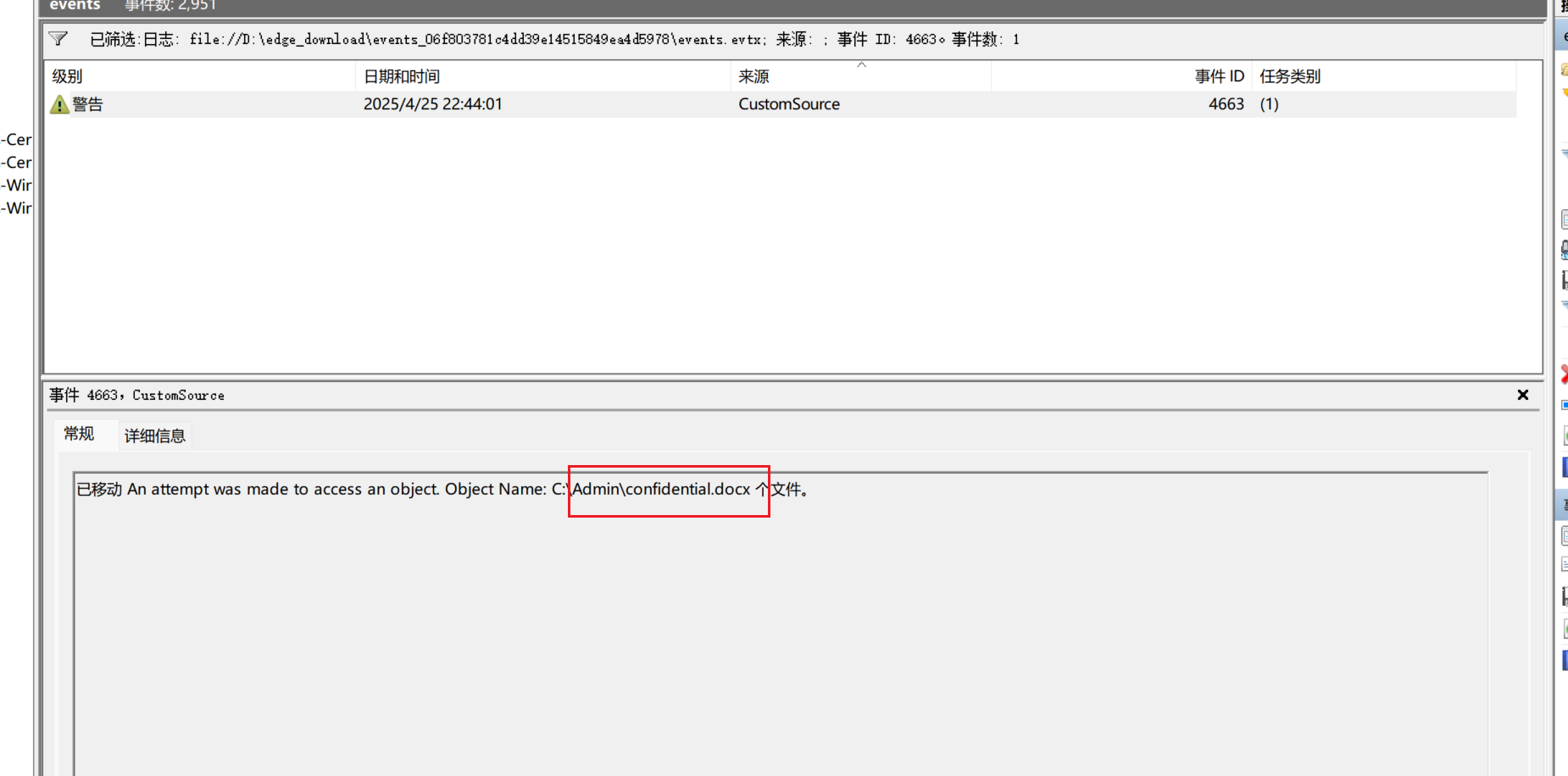
定位到这个
flag{confidential.docx}
RuneBreach

ida打开发现沙箱
禁用了execve,无法正常shell拿flag
考虑orw open read write
看程序流程
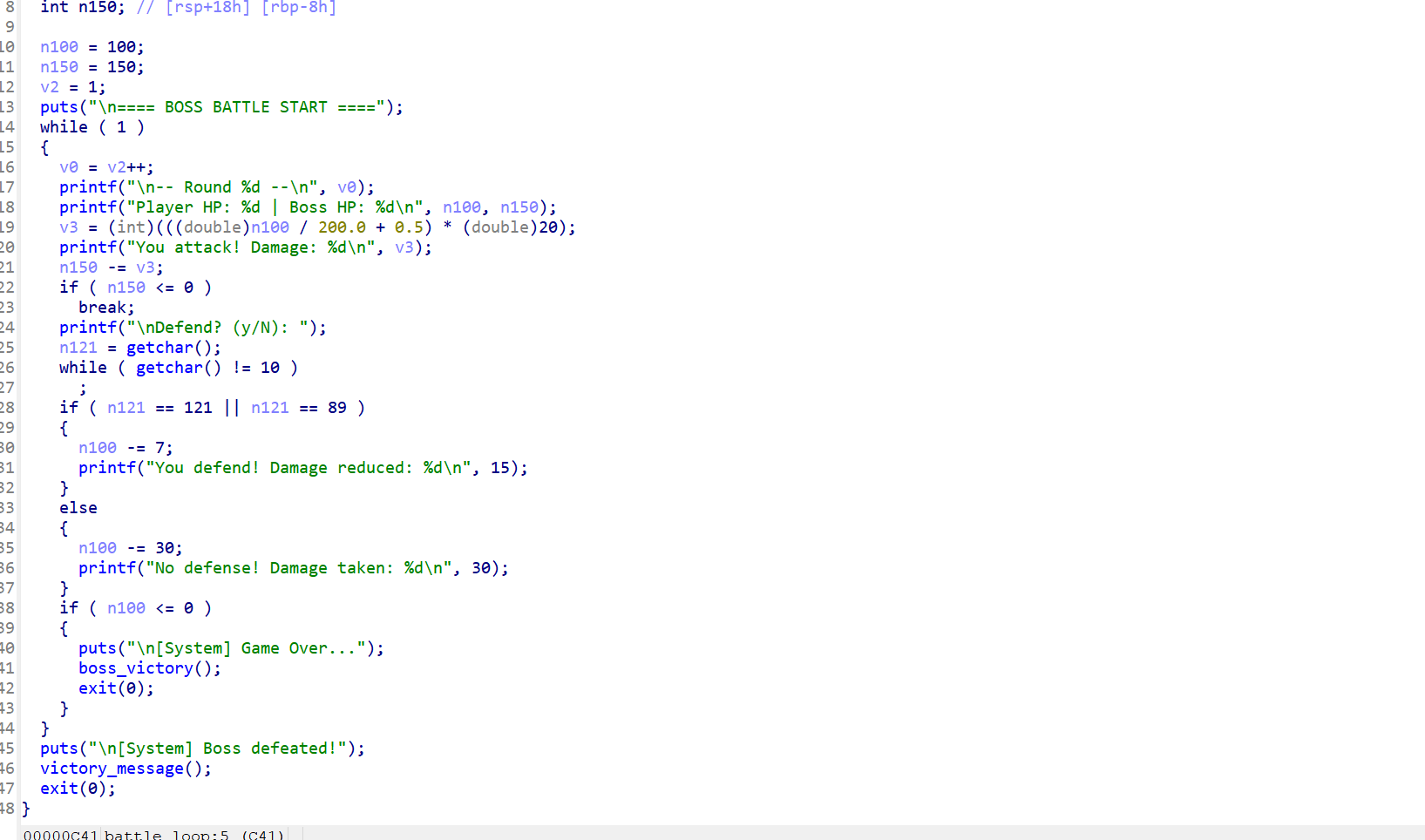
输入4次y之后进入
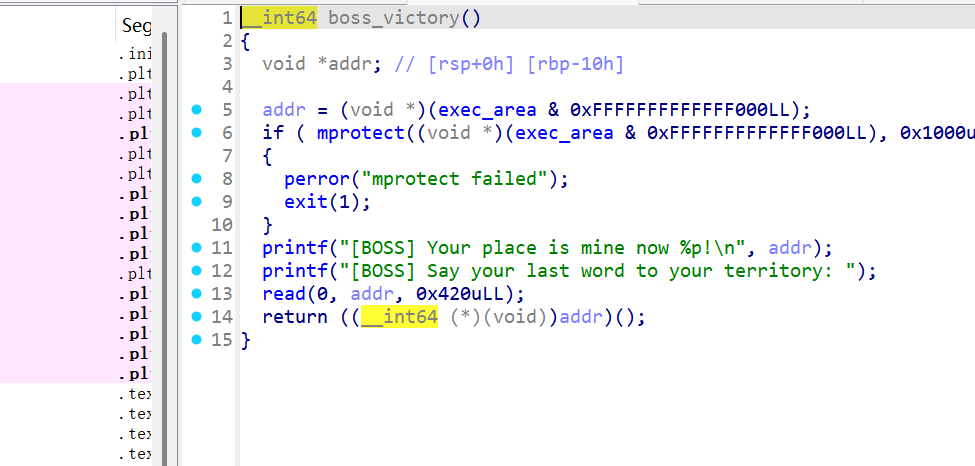
利用这一部分read写shellcode打orw
exp:
1 | from pwn import * |
黑客密室逃脱
点点点
发现密文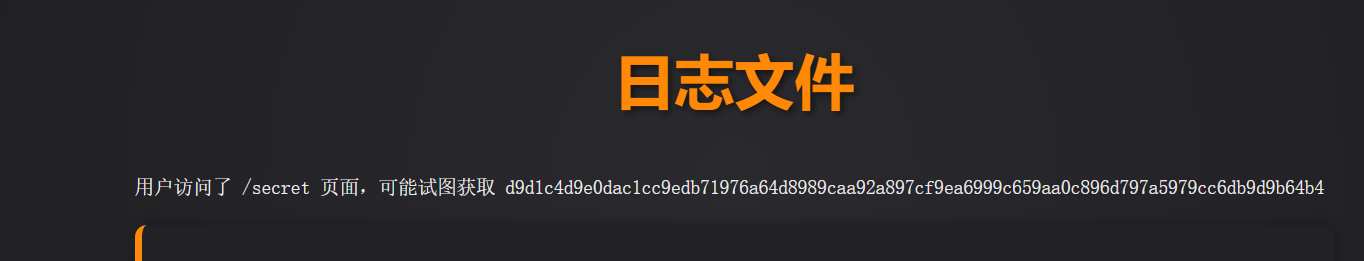
记录下来

爆破文件目录
得到flask框架,访问框架源码app.py
得到
1 | import os |
发现有一个hidden.txt文件,访问得到key

根据得到的源码写解密脚本
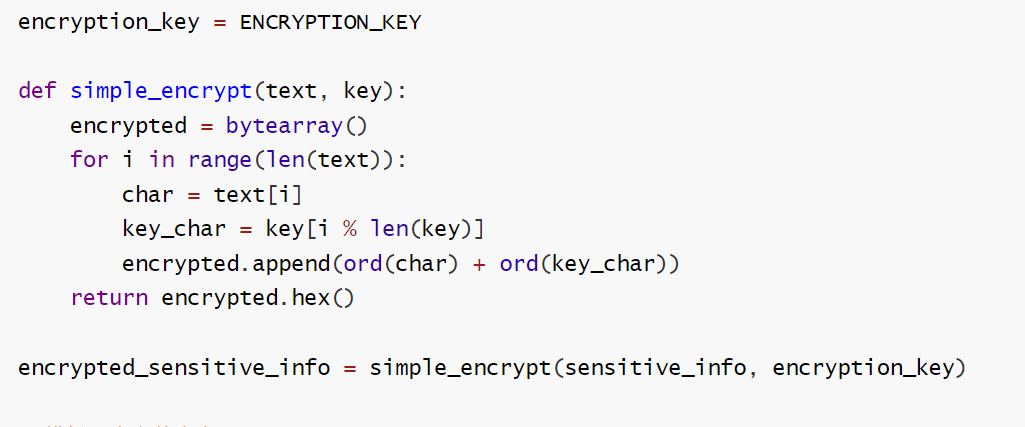
exp:
1 | from contourpy.util.data import simple |
flowzip
流量包,wireshark打开里面有100个压缩包
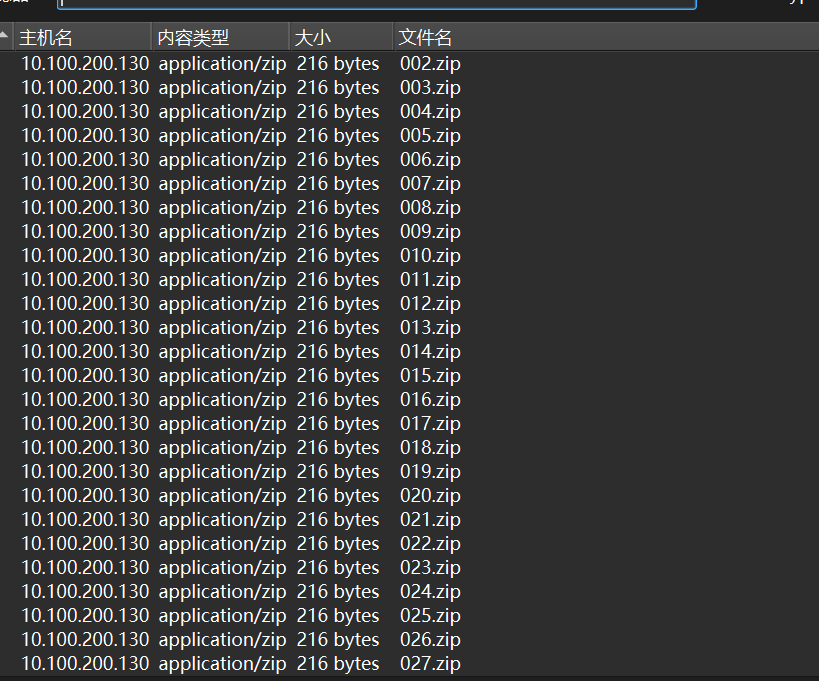
发现有一个大小不一样得压缩包
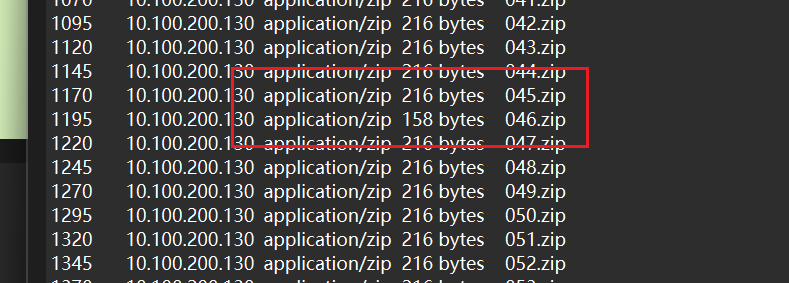
导出
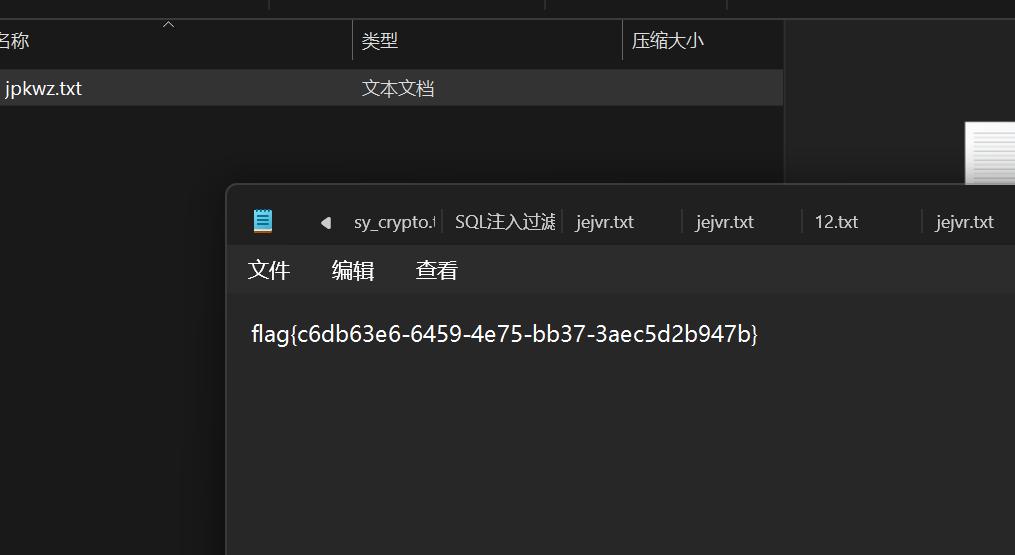
得到flag{c6db63e6-6459-4e75-bb37-3aec5d2b947b}
easy_AES
题目给出以下信息:
gift: 一个整数
64698960125130294692475067384121553664key1_hex: AES密钥的十六进制字符串
74aeb356c6eb74f364cd316497c0f714cipher_hex: 经过两次AES加密后的密文
1
2
3
4
5'''
gift = 64698960125130294692475067384121553664
key1 = 74aeb356c6eb74f364cd316497c0f714
cipher = b'6\xbf\x9b\xb1\x93\x14\x82\x9a\xa4\xc2\xaf\xd0L\xad\xbb5\x0e|>\x8c|\xf0^dl~X\xc7R\xcaZ\xab\x16\xbe r\xf6Pl\xe0\x93\xfc)\x0e\x93\x8e\xd3\xd6'
'''目标是恢复出另一个密钥
key0,解密密文得到以flag{开头的明文。1
key0_nibble[i] & key1_nibble[i] = gift_nibble[i]
思路:
gift_nibble是将 gift 转为128位二进制后分割为32个4位片段得到
拆分半字节数组将 gift 转换为128位二进制,分割为32个4位的 gift_nibbles。
将 key1_hex 转换为32个半字节数组 key1_nibbles。
计算每个位置的候选值 对每个位置 i,
计算所有满足 x & key1_nibbles[i] = gift_nibbles[i] 的 x 值(即可能的 key0 半字节值)。
分组交叉约束将 key1 中相同值的半字节位置分组。
对每组,取其所有位置候选值的交集,形成每个 key1 半字节值对应的候选 key0 半字节集合。
回溯搜索合法解按候选集大小升序处理(剪枝优化),尝试为每个 key1 半字节值分配唯一的 key0 半字节。
构造 key0_hex,验证双重AES解密结果是否为合法Flag格式。
脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
from collections import defaultdict
# 已知数据
gift = 64698960125130294692475067384121553664
key1_hex = "74aeb356c6eb74f364cd316497c0f714"
cipher_hex = ("36bf9bb19314829aa4c2afd04cadbb35"
"0e7c3e8c7cf05e646c7e58c752ca5ab"
"165e722..."
).replace(" ", "")
cipher = bytes.fromhex(cipher_hex)
# 将 gift 转换为 32 个 nibble (4-bit)
gift_bin = format(gift, '0128b')
gift_nibbles = [int(gift_bin[i*4:(i+1)*4], 2) for i in range(32)]
# 提取 key1 的 nibbles
key1_nibbles = [int(key1_hex[i], 16) for i in range(32)]
# 生成每个位置的候选 x 值
pos_cands = []
for i in range(32):
m = key1_nibbles[i]
b = gift_nibbles[i]
pos_cands.append([x for x in range(16) if (x & m) == b])
# 按 key1 的 nibble 分组并求交集
positions_by_y = defaultdict(list)
for i, y in enumerate(key1_nibbles):
positions_by_y[y].append(i)
y_cands = {}
for y, poses in positions_by_y.items():
common = set(pos_cands[poses[0]])
for p in poses[1:]:
common.intersection_update(pos_cands[p])
y_cands[y] = list(common)
# 回溯搜索有效反置换
inv_map = {}
solutions = []
# 按候选数升序排列以优化搜索
items = sorted(y_cands.items(), key=lambda kv: len(kv[1]))
def dfs(idx):
if idx == len(items):
key0_nibbles = [inv_map[y] for y in key1_nibbles]
key0_hex = "".join(f"{n:x}" for n in key0_nibbles)
if len(key0_hex) != 32:
return False
try:
aes1 = AES.new(bytes.fromhex(key1_hex), AES.MODE_CBC, bytes.fromhex(key0_hex))
aes0 = AES.new(bytes.fromhex(key0_hex), AES.MODE_CBC, bytes.fromhex(key1_hex))
intermediate = aes1.decrypt(cipher)
plaintext = unpad(aes0.decrypt(intermediate), 16)
if plaintext.startswith(b"flag{"):
print("Success! Key0:", key0_hex)
print("Flag:", plaintext.decode())
solutions.append((key0_hex, plaintext))
return True
except:
pass
return False
y, candidates = items[idx]
for x in candidates:
inv_map[y] = x
if dfs(idx + 1):
return True
del inv_map[y]
return False
# 启动搜索
if dfs(0):
print("解密成功!")
else:
print("未找到有效解,请检查输入数据。")
ECBTrain
环境nc连上
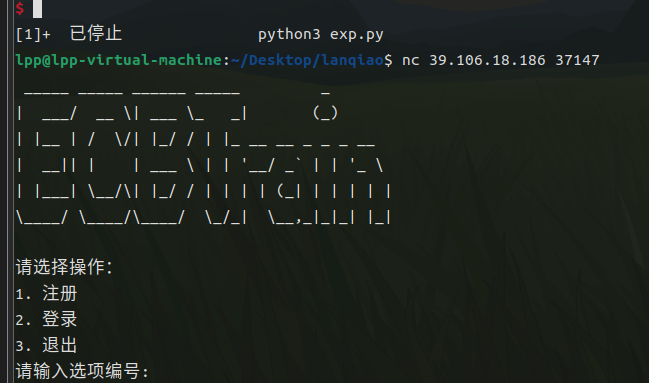
测试一下说要以admin身份登录
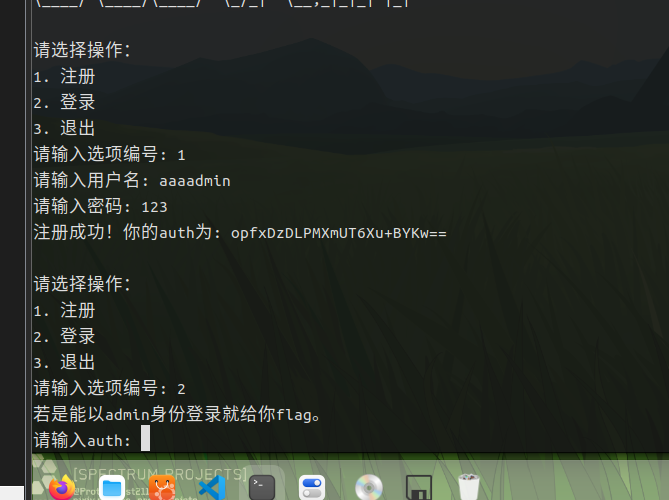
auth输出base64
exp:
1 |
|
将输出得东西输入登录回去
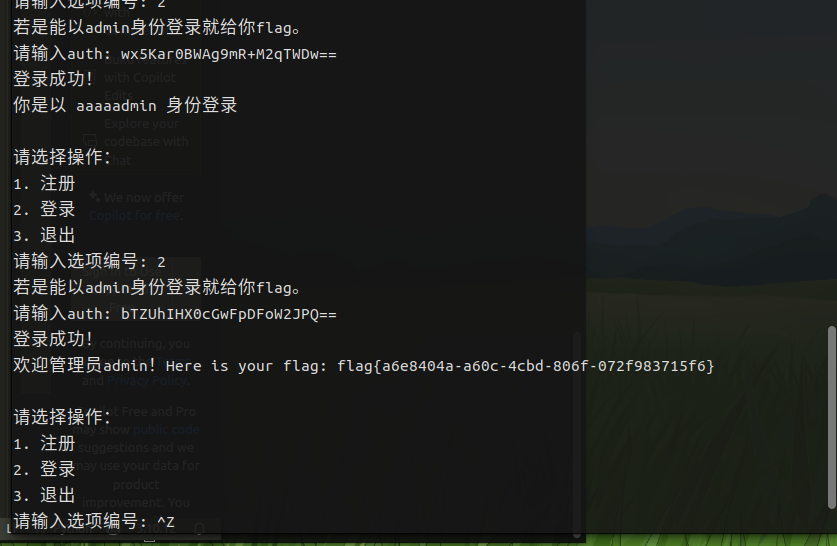
getflag
- Title: 2025蓝桥网络安全 wp
- Author: luyanpei
- Created at : 2025-04-27 00:07:05
- Updated at : 2025-05-14 20:44:47
- Link: https://redefine.ohevan.com/2025/04/27/2025蓝桥网络安全/
- License: All Rights Reserved © luyanpei